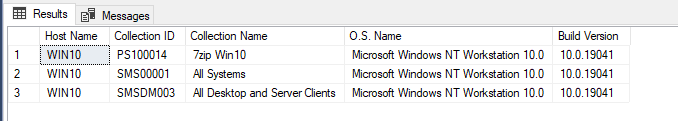
##Read the offersum box for SVF Files
$configMgrBoxpath = "E:\Temp\offersum Files TO scan"
$count = O
Get-ChildItem -Path $configMgrBoxpath -Include *.SVF -Recurse -Force -ErrorAction
Silentlycontinue -outBuffer 1000 | ForEach-Object {
$File = $_.FullName;
$count = $count + 1
If (($count % 1000) -eg 0) {
write-host $count "files scanned"
try {
( ##Search for the non-existing deployment id passed in below select string within the SVF File
Get-content _ReadCount 1 _TotalCount 6 -Path $_.FullName _ErrorAction Stop |
select-String _Pattern ('2147024894') -ErrorAction stop
).Matches.Result($File)
} catch {
##write-warning -Message "Given deployment id not found in SFi1e"
}
##Write the non-existing deployment SVF file location on a text file
} | move-iten -Force -destination "E:\Temp|Offersum Files Irrelvent"
write-host "Script Finished !!!"